Building & Testing Lambda@Edge Functions with LocalStack
AWS FOR THE REAL WORLD
⏱️
Reading time: 8 minutes
🎯
Main Learning: Building & Testing Lambda@Edge Functions with LocalStack
Hey Reader 👋🏽
we hope you have a great week! End of last year the CDN Edgeio was deprecated. Tobi's client company used it and the only thing that saved his day was CloudFront and Lambda@Edge Functions. But we realized that testing them and executing them locally is a pain. When we started to look for a solution we found Localstack - let's see how we can use it to debug our functions. IntroductionLet's be honest: debugging CloudFront or Lambda@Edge functions is still a pain. With LocalStack, this changes. In this blog post, we'll look at how to do this. LocalStack SetupGetting started with LocalStack is easy. On macOS, you can install it using Homebrew:
TERMINAL
The tutorials for other operating systems can be found on the official documentation. After the installation, let's check if LocalStack is running:
TERMINAL
If you see something like this, you're good to go!
TERMINAL
This will pull the latest docker image and start LocalStack. 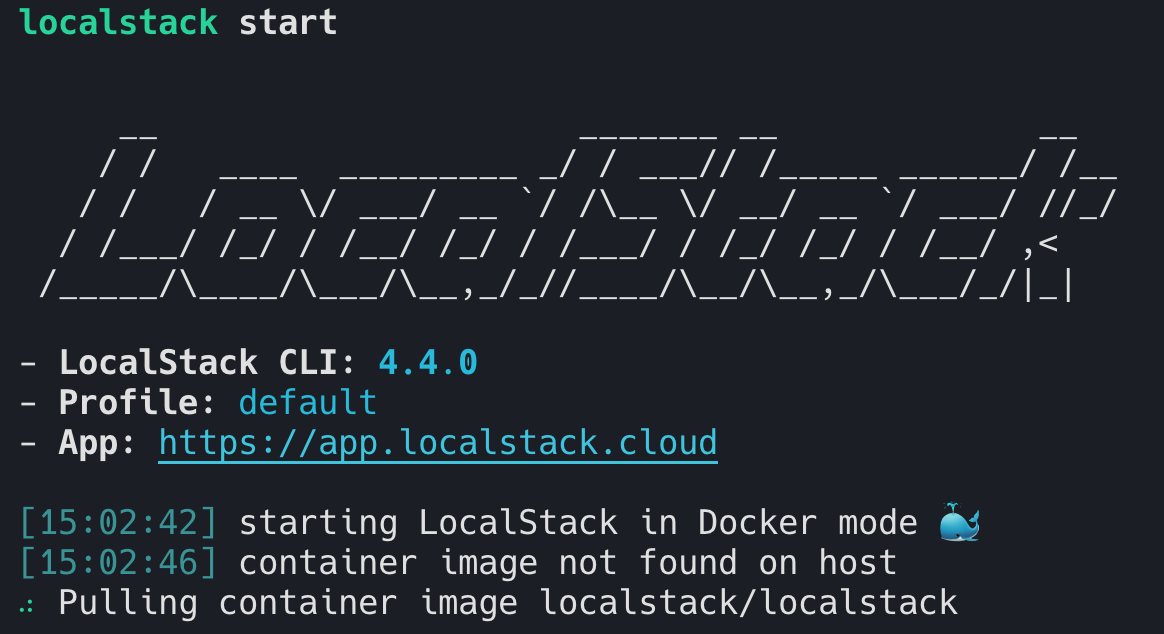
LocalStack will print a We'll need to create an account to use the dashboard. Afterwards, let's continue with the set up by clicking on the 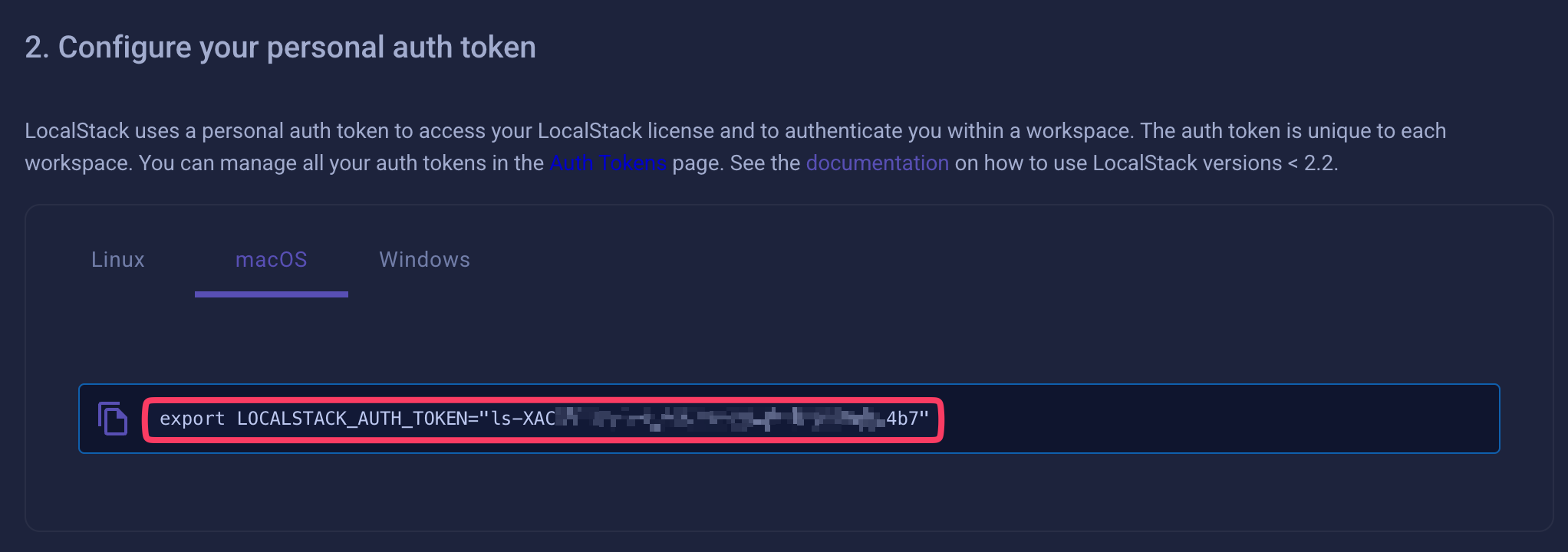
We can now export the Auth Token:
TERMINAL
This will set the Auth Token for LocalStack. Upgrading our License to the Base PlanFor using CloudFront, we need to upgrade our license to the base plan. Let's jump to the pricing page of LocalStack and click on the Don't worry: the Base Plan can be tested for 14 days for free! Please restart LocalStack after adding your Auth Token and upgrading your license. Afterwards, you should also see that your local instance is running the dashboard! 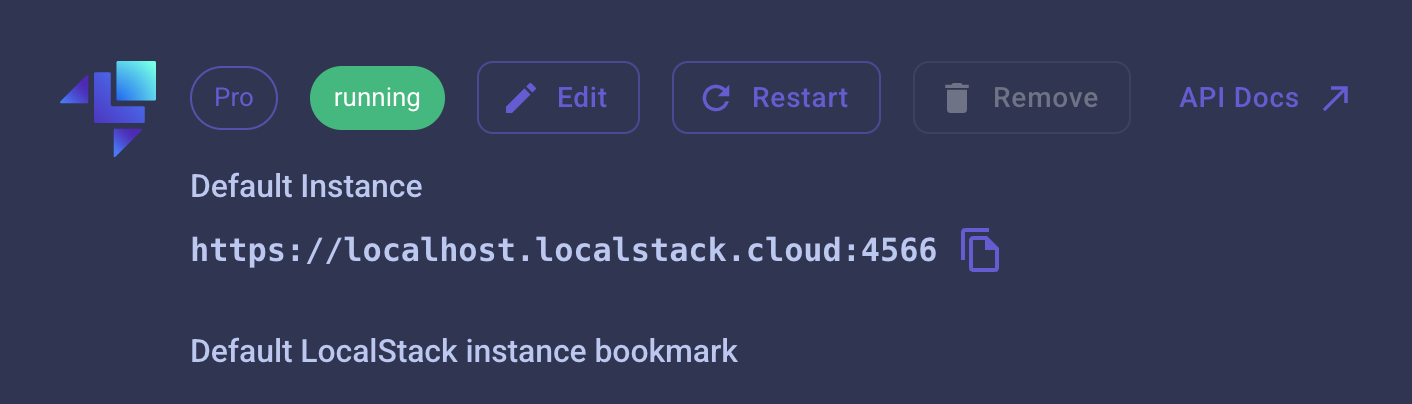
Using the LocalStack CLINow we're ready to use the LocalStack CLI. It's a powerful tool that allows us to manage our LocalStack resources. Let's create a bucket:
TERMINAL
Instead of sending the command to the real AWS API, it will be redirected to our locally running LocalStack instance. In the terminal window where LocalStack is running, you should see something like this:
TEXT
This means that the bucket was created successfully. Let's list our buckets to verify that:
TERMINAL
Yay, our setup works as expected and our bucket is listed! You can also install
TERMINAL
This will install the
TERMINAL
This will list our buckets as expected - no need to pass the specific endpoint anymore. Creating a Lambda@Edge FunctionBefore we want to create our CloudFront distribution, we need to create our Lambda function first. What do we need for this?
Let's start with the trust policy.
TERMINAL
Next, we'll create the role that will be used by the function.
TERMINAL
Now we can put our handler code into a file.
TERMINAL
If the request originates from CloudFront, the If it's any other invocation, we'll simply return a HTTP 200 and a static message. Great! Now we can actually create the function.
TERMINAL
This will create the function and print the whole configuration in the response. Let's test our function by invoking it.
TERMINAL
This will invoke the function and print the response in the Let's use
TERMINAL
This will print the response in the Now that this works, let's update the function in a way so that we can use it in our CloudFront distribution.
TS
Let's now create the zip file again with the new code and update the function.
TERMINAL
As only published functions can be attached to a distribution, we need to publish our function first.
TERMINAL
This will publish the function and print the version. Any new publish will increase the version number, which means we need to update our distribution configuration. Creating a CloudFront DistributionNow we're ready to create a CloudFront distribution. Let's create a simple
JSON
Make sure to put your correct versioned function ARN in the In this distribution, we're using the type Now we're ready to create our distribution:
TERMINAL
This will create a new distribution and print the domain name of the distribution. Let's put a simple HTML file into our bucket and see if it's working.
TERMINAL
This will upload the file to our bucket and set the ACL to public-read. Let's try to access the file via the CloudFront distribution:
TERMINAL
This should return the content of the
Let's check if the response contains the
TERMINAL
Great! Our function is working as expected. Let's also check that our created distribution, S3 bucket and Lambda function are listed in the dashboard. Let's click on 
Iterating our Lambda@Edge FunctionNow that we know that our function is working as expected, let's iterate on it. Let's say we want to add a new header to the response. What do we need to do?
Currently, LocalStack does not support updating the distribution's Edge Function configuration via the CLI. Let's change our handler code to add another new header:
TS
Now, we need to create a new zip file and update the function:
TERMINAL
Now we just need to put the new version ARN into our
TERMINAL
Let's run our cURL command again to see the new header:
TERMINAL
Awesome! We've just iterated on our Lambda@Edge function in a few seconds. Also, without the risk of breaking anything real.
ConclusionIn this blog post, we've looked at how to build, test, and debug Lambda@Edge functions with LocalStack. We've created a simple CloudFront distribution and Lambda@Edge function and iterated on it in a few seconds. Doing this with a real distribution would take several minutes. And LocalStack doesn't stop here. SummaryThat's it for this newsletter! We showed how to use LocalStack to build, test, and debug Lambda@Edge functions locally in your own terminal, so you can cut down those painful CloudFront waits and dodge those oh-no deployment breaks. Have you given LocalStack a spin yet?See you soon 👋🏽 Sandro & Tobias |
AWS for the Real World
We teach AWS for the real world - not for certifications. Join more than 10,500 developers learning how to build real-world applications on AWS.
AWS FOR THE REAL WORLD ⏱️ Reading time: 8 minutes 🎯 Main Learning: How to securely connect Claude Code to a private RDS database using MCP, SSM tunnels, and VPC endpoints 📝 Blog Post 💻 GitHub Repository 🎬 Watch on YouTube Hey Reader 👋🏽 AI coding assistants are great. If you give them the right context. Your database schema is one of the most valuable pieces of context you can provide. But there's a problem: your RDS is in a private subnet. As it should be. So how do you connect Claude Code to...
AWS FOR THE REAL WORLD ⏱️ Reading time: 8 minutes 🎯 Main Learning: How to pause Step Function workflows for human approval using the callback pattern 📝 Blog Post 💻 GitHub Repository 🎬 Watch on YouTube Hey Reader 👋🏽 I've used this pattern in almost every project I've built. Whenever you need a human in the loop - approvals, reviews, manual checks - and you still want to see what's happening, Step Functions are perfect. Lambda is my go-to for almost everything. APIs S3 triggers event consumers...
AWS FOR THE REAL WORLD ⏱️ Reading time: 5 minutes 🎯 Main Learning: How to make Claude write production-ready Terraform instead of technical debt 🎬 Watch on YouTube 📝 Blog Post 💻 GitHub Repository Hey Reader 👋🏽 We've been heads-down the past weeks. Preparing the live AMA workshops from Black Friday (sorry for the delay!) and recording new YouTube videos. It's been a lot of fun. Speaking of videos - this week Tobi recorded one you'll want to watch. Here's the problem: LLMs want to close the...