🔒 Create a Secure Landingzone from Scratch (Terraform Examples Included!)
AWS FOR THE REAL WORLD
⏱️
Reading time: 17 minutes
🎯
Main Learning: How to build a secure, scalable AWS landing zone using AWS Organizations, Service Control Policies, and Identity Center for centralized account and user management.
Hey Reader 👋🏽
Today I want to dig into how to set up a proper AWS landing zone. We’ll be chatting about AWS Organizations, Service Control Policies (SCPs), and Identity Center. These are the core tools I reach for when I need to get accounts organized, access locked down, and teams working smooth. If you’ve ever found AWS accounts getting out of hand, this one’s for you. Let’s get right into it! This is sponsored content supporting our AWS & serverless content Setting up AWS for enterprise use is a mess. Or even for any solo developer that wants to use AWS in some kind of professional way. You start with one account, add another for staging, then production needs its own account. Suddenly you're juggling IAM users, access keys, and policies across five different accounts. Everyone "shares" the dev environment because setting up proper permissions takes too long. I was not only once in the position where somebody started with everything in one account and tried to manage permissions with resource name prefixes.
You know, When we finally decided to migrate to separate accounts, we knew it would be a pain. Production was already running (= customers were using the system). We couldn't just shut everything down and rebuild it. The migration is quickly taking weeks or months. We had to build a parallel infrastructure in new accounts while keeping the old stuff running. The lesson: it's much harder to fix a broken AWS setup than to start with a proper one. In this article, I'll show you how to build a proper AWS landing zone that actually works. Not overcomplicated, but still secure, highly customizable and easy to maintain. This setup will take you some time to implement properly, but it'll save you months of migration headaches later. And you'll learn the key concepts of AWS Organizations, Service Control Policies and Identity Center. And how they work together to build a secure and scalable AWS environment. No fluff, no BS, just the facts. 🤝 What You'll Learn
The Problem with Ad-Hoc AWS SetupsMost teams start with a single AWS account. Then they need staging, so either they put everything into the same account or they create another account. Production definitely needs its own account for security. Suddenly you have multiple accounts, each with...
Sound familiar? 💭 I've been there, not just once but multiple times. Not just in small startups (or my own indie projects), but also large enterprises that do lack fundamental AWS knowledge (or the will to do things right) to some extend. Let's jump into how to do it right; directly from the beginning! Part 1: AWS Organizations - Your Account Management FoundationThe most important part of the AWS Landing Zone is the AWS Organizations. It will help you to easily work with multiple accounts, users, permissions and services. Let's start with the management account. The management account is the central account that is used to manage the organization. It's also the account that you use to create the organization. It has complete access to all AWS resources and services. 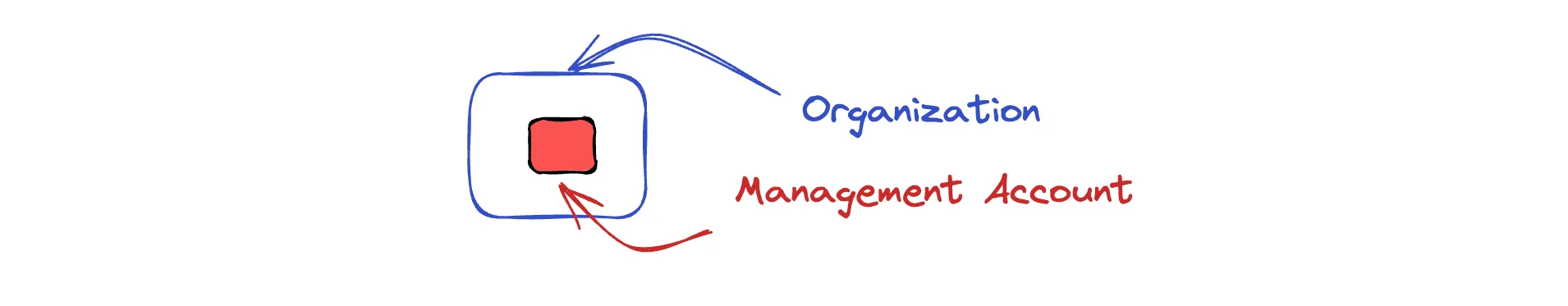
Creating an organization is easy. Just go to the AWS Organizations console and click on "Create Organization". You'll create the organization in the region that you've selected. But don't worry. When you work with AWS Organizations you’re interacting with a global control plane—not a region-specific service. Choosing a region really only affects the endpoint you use; the Organizations data (accounts, policies, invitations, etc.) lives globally. As this account will be the organization's management account, it's important to keep it secure. Most importantly, use a strong password and enable MFA. At best, use a hardware key instead of your phone. If you want a real-world walkthrough, we wrote up the whole in another detailed article: How to actually secure your AWS account with MFA.
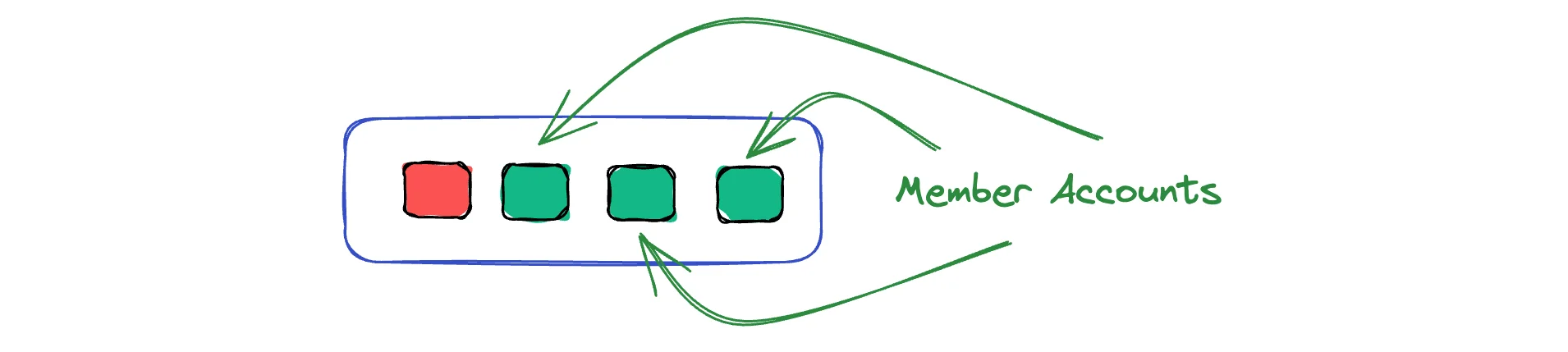
Now that our organization's root is created, we can simply add member accounts. Not by registering new accounts, but by simply using the AWS Organizations console.
When we have multiple accounts, we can create organizational units (OUs) to group them. This is useful to manage permissions and services in a more granular way. 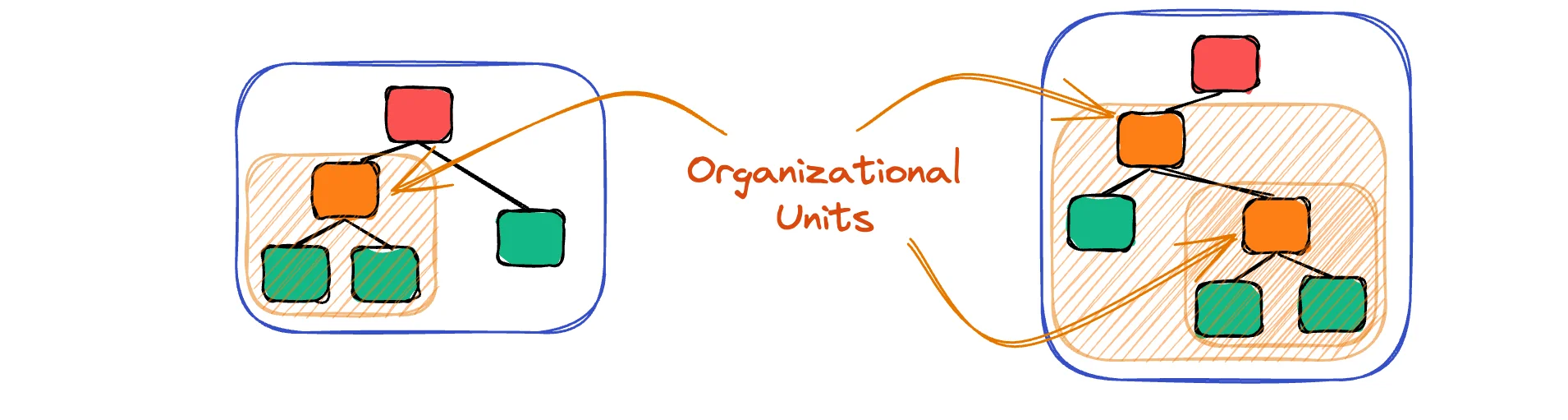
For example, we can create an OU for Building It With TerraformHere's how I actually implemented my own AWS Landing Zone using Terraform. Instead of clicking through the AWS console, I built a reusable module that sets everything up automatically.
HCL
The key here is enabling Then I create accounts programmatically:
HCL
Pro tip: Use different email addresses for each account.
I use email aliases like Instead of updating things manually in the console when you need changes, you just update your Terraform code and apply it. Need a new account? Add it to your code. Want to reorganize your OUs? Update the Terraform and run it. The Complete Setup ProcessLet me walk you through the entire process from start to finish. This is exactly how I set up organizations for my own projects: 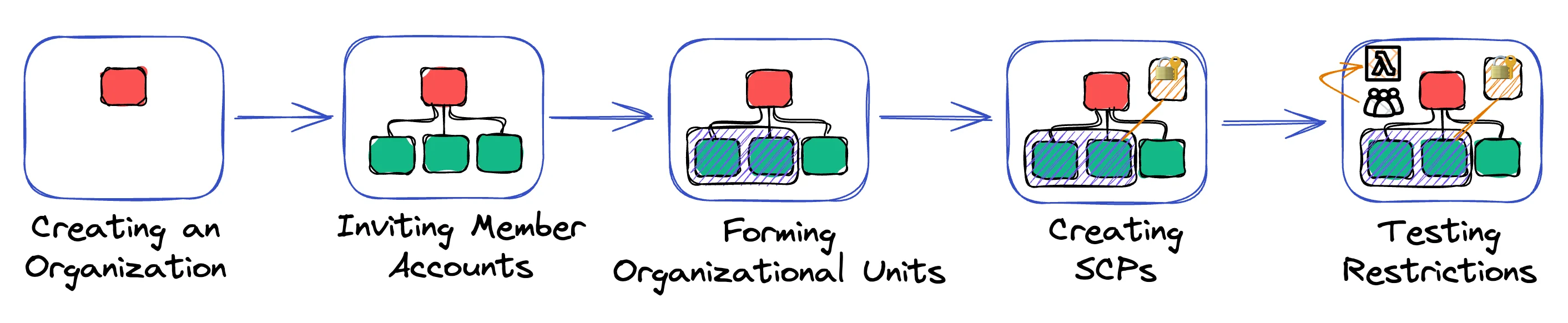
This process takes about a day if you're doing it manually, or a few hours with Terraform. The key is to go step by step and test everything before moving to the next step. Part 2: Service Control Policies (SCPs) - The Guardrails You Actually NeedHere's something that will help you sleep better at night: knowing that even if someone gets admin access to your AWS accounts, they can't do the really dangerous stuff. You've probably seen the horror stories online - developers waking up to $10k bills because someone spun up mining instances, or entire databases getting deleted because someone thought they were in the test environment. SCPs are like having a security guard at the door of your AWS accounts. Even if someone has a VIP pass (admin permissions), the security guard can still say "nope, you're not doing that." They don't give permissions, they just block the scary stuff. What SCPs Actually DoSCPs are basically a filter. Whatever permissions someone has through IAM, SCPs can block specific actions. Even if you're the root user of an account, SCPs can stop you from doing stupid things. Here's the thing: SCPs are deny-only. They can't give you permissions, only take them away. Your IAM policies grant access, SCPs restrict it. For example:
Creating Your First SCPLet's create an SCP that blocks all EC2 instance launches. This makes sense if you're running serverless services and don't need EC2 at all.
Now create a new policy called "DenyAllEC2":
JSON
This policy blocks anyone from launching any EC2 instances. Perfect if your entire setup runs on Lambda, containers, or other managed services. Enforce MFA for Identity Center UsersHere's another useful SCP that enforces MFA for all Identity Center users. This means people can't access AWS without multi-factor authentication enabled.
JSON
This forces everyone to use MFA before they can do anything meaningful in AWS. No more "I'll set up MFA later" excuses. Applying SCPs to Your OrganizationOnce you've created an SCP, you need to attach it somewhere. You can attach SCPs to:
I'd recommend starting with a single test account first. Create a throwaway account, attach your SCP, and see if it actually blocks what you expect. Once you're confident it works, apply it to your development OU. Applying SCPs with TerraformHere's how I manage SCPs in my Terraform setup. Instead of clicking through the console, you can define policies as code:
HCL
Pro tip: Use the For the MFA enforcement policy:
HCL
When you manage SCPs with Terraform, you get version control for your policies.
You can see exactly when policies changed and who changed them.
Rollbacks become Testing Your SCPsHere's how to test if your SCP actually works:
For our EC2 blocking policy, try launching any EC2 instance. You should see something like: "You are not authorized to perform this operation." If you don't get an error, your SCP isn't working. Check that it's attached to the right OU or account. Testing SCPs is painful because you can't debug them locally. You attach them, try something, get a cryptic error, modify the policy, wait for propagation, and try again. Rinse and repeat N times. Now I always:
SCPs are powerful, but expect to spend way more time debugging them than you think. How SCPs Are AppliedUnderstanding where SCPs can be attached is crucial for getting them right: 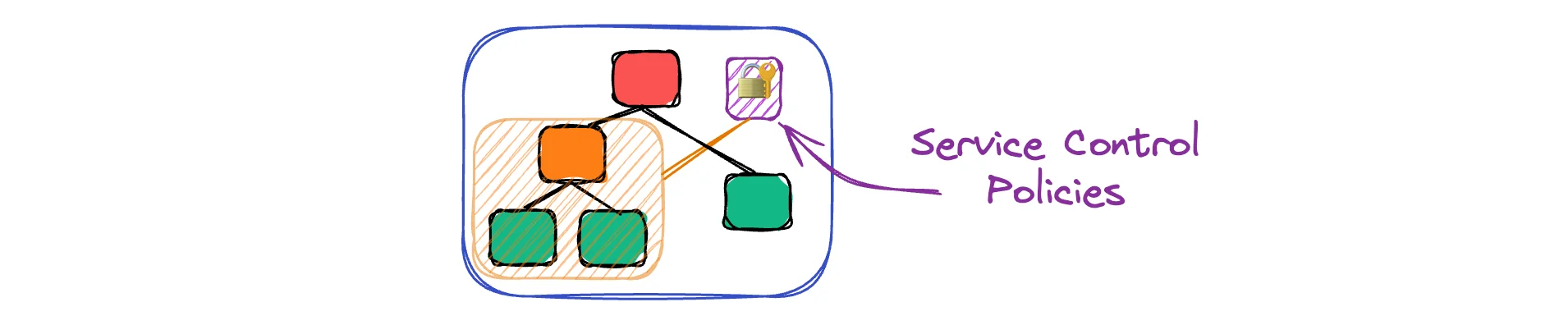
You can attach SCPs to:
The key insight: SCPs are inherited down the tree. If you attach an SCP to the root, it applies to every account in your organization. If you attach it to an OU, it applies to all accounts in that OU. Understanding Root User PermissionsHere's something critical that trips up a lot of people: 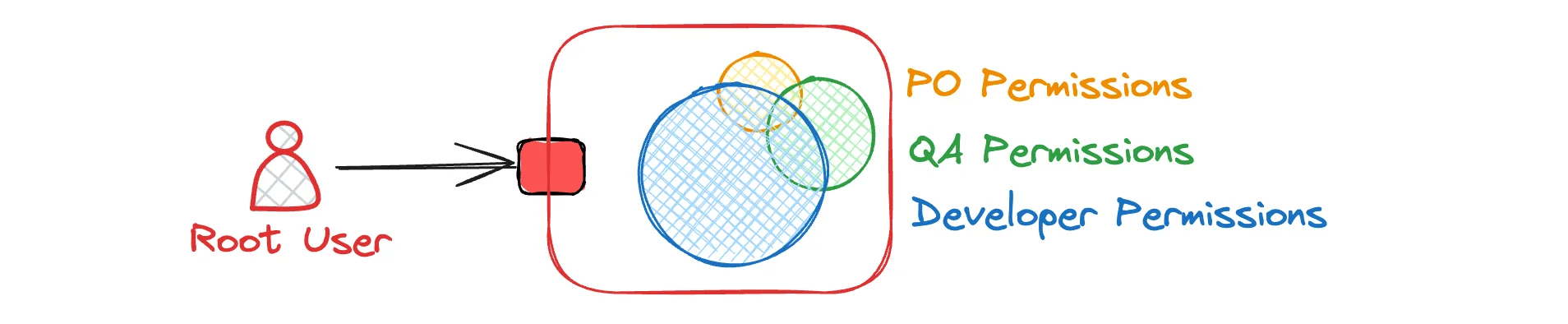
The Gotchas with SCPsSCPs have some weird behavior that'll bite you: 🛡️ Management Account Immunity: SCPs don't affect the management account. That account can do whatever it wants, always. 🔒 Default Deny: By default, everything is denied until you attach the "FullAWSAccess" policy. Don't accidentally remove this from the root unless you want to lock everyone out. 📏 Policy Size Limits: SCPs have a 5,120 character limit. If your policy gets too complex, you'll need to split it up. 🧪 No Local Testing: You can't test SCPs locally. You have to apply them and see what breaks. Always test in a sandbox account first. When SCPs Actually HelpSCPs shine in a few specific scenarios:
They're not magic. They won't solve bad IAM design or replace proper training. But they'll catch the obvious mistakes before they become expensive problems. Part 3: AWS SSO & Identity Center - User Management That Doesn't SuckManaging users across multiple AWS accounts is a nightmare.
Even as a solo developer, you end up with different IAM users for dev, staging, and production.
Each with their own access keys sitting in your Or maybe you're working with a small team where everyone just uses the same shared credentials. "Just put the keys in the team Slack" becomes the unofficial onboarding process. It's a mess. AWS Identity Center (formerly SSO) fixes this. One login for all your accounts, whether you're flying solo or managing a team of 50. No more credential juggling. What Identity Center Actually DoesIdentity Center acts as a central authentication hub. Users log in once and get access to multiple AWS accounts. They assume different roles in different accounts without managing separate credentials. Here's what it replaces:
Setting Up Identity CenterIdentity Center only works if you have AWS Organizations set up first. You can't use it with standalone accounts.
Important: Once you enable Identity Center in a region, you can't move it. Choose carefully. Creating Your First UserYou can create users directly in Identity Center or connect to external identity providers like Active Directory or Google Workspace. I'll show you the simple approach first.
That user now exists in Identity Center but can't access any AWS accounts yet. You need to create permission sets. Permission Sets - The Key to Sane Access ControlPermission sets define what someone can do in an AWS account. They're basically IAM roles with a friendlier interface. Let's create a permission set for developers:
PowerUserAccess gives broad access but blocks IAM changes. It's perfect for developers who need to build things but shouldn't mess with permissions. Assigning Users to AccountsNow comes the magic part. You assign users to accounts with specific permission sets.
Repeat this for your production account, but maybe with a more restrictive permission set. Automating Identity Center with TerraformWhile the initial Identity Center setup must be done manually (enabling it in the console), you can manage users, permission sets, and assignments with Terraform:
HCL
To assign users to accounts with specific permission sets:
HCL
Note: You can also get the SSO instance ARN programmatically with a data source:
HCL
With this setup, almost anything can be automated. But permission sets and assignments can be fully automated. The User ExperienceOnce everything is set up, here's what your users see:
No more juggling multiple sets of credentials. No more "which account am I in again?" Connecting to External Identity ProvidersIf you already have users in another system, you can connect Identity Center to external identity providers like Azure AD or Auth0. 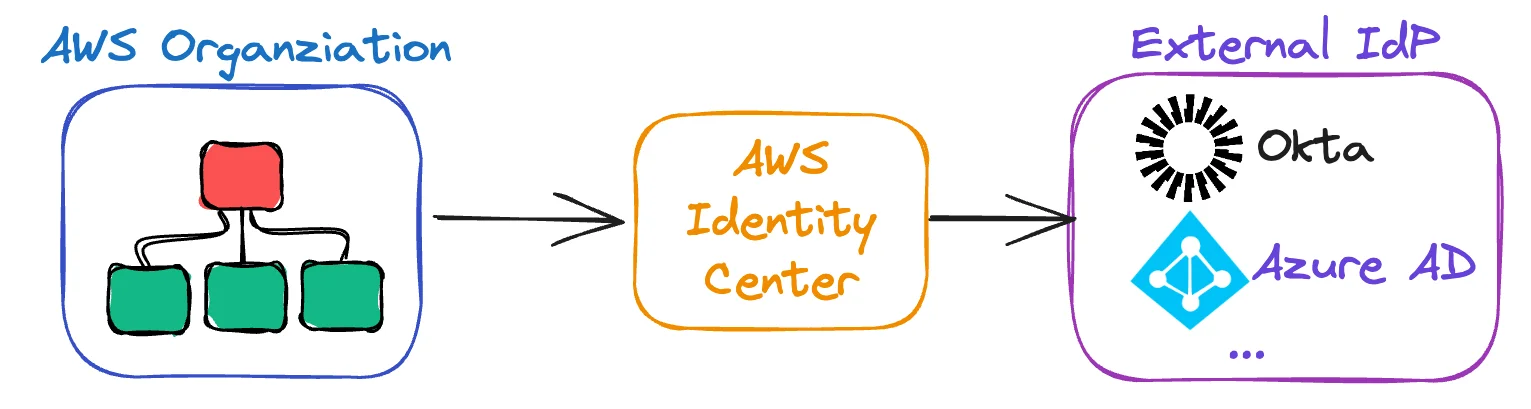
The setup can be tricky, but it means users don't need yet another login. What About CLI Access?Developers need CLI access, not just console access. Identity Center handles this, but there are a few ways to do it. Option 1: AWS CLI v2 (built-in)
After setup, developers run Option 2: Leapp.cloud (recommended) If you want something that actually works well, check out Leapp.cloud. It's the best credential management tool for AWS, Azure, and GCP. Handles SSO sessions, role switching, and credential management way better than the native CLI tools. Plus it has a nice GUI so you don't have to remember commands. The Limitations You'll HitIdentity Center isn't perfect. Here are the gotchas you'll run into:
Nevertheless, Identity Center is always the way to go! The Real BenefitsAfter setting up Identity Center properly, you'll notice:
The setup takes a few hours, but it saves weeks of credential management later. Part 4: How It All Works TogetherNow you've got three pieces: Organizations, SCPs, and Identity Center. Separately, they're useful. Together, they create a system that actually scales. Most people struggle to understand how accounts, groups, and permission sets work together. Let me explain it with an analogy that actually makes sense. Think of It Like a Company with Multiple OfficesImagine your AWS setup is like a company with different offices around the world: 🏢 Accounts (Offices) 👥 Users (People) 🏷️ Groups (Job Roles) 🔑 Permission Sets (The Keys) How It Works in PracticeEmployee → joins Group → gets Permission Set → accesses specific Offices Example: Carol is in the The admin Frank is in the With Identity Center: Everyone logs in once and can switch between the offices they're allowed to enter. No need for separate keys for every door. With SCPs: Even if Frank has admin access, the office security system (SCP) can still block certain dangerous actions, like "no one can use the paper shredder in any office." My Mental Model Breakdown (And How the Office Analogy Saved Me)When I first set up Identity Center, I spent three weeks completely confused about how users, groups, and permission sets actually worked. Coming from traditional IAM, I kept thinking in terms of "users get policies attached directly." So when I created my first user in Identity Center, I immediately went looking for where to attach IAM policies. There was no such option. Instead, I found something called "permission sets". Okay, so permission sets are like IAM roles, right? I created a permission set called "DeveloperAccess" with PowerUserAccess attached. Then I tried to assign it to my user. The interface wanted me to pick both a user AND an account. Why do I need to pick an account? In regular IAM, you just attach policies to users and they work everywhere in that account. I assigned my user the DeveloperAccess permission set for my sandbox account. Then I logged into Identity Center and tried to access my production account. Nothing there. The user could only see the sandbox account. So I went back and assigned the same permission set to the same user for production. Now they could access both accounts, but with identical permissions. What if I wanted them to have read-only access in production but full developer access in sandbox? I created another permission set called "ReadOnlyAccess". Then I had to go back and change the assignment for production. But now I had two permission sets doing almost the same thing. The breaking point came when I needed to add a new developer. I had to:
Multiply this by five developers, and I had 15 different assignments to manage. Every time I added a new account, I had to remember which permission set each person should get for that specific account. Then I read about groups. Finally! Groups would solve everything. I'd create a "developers" group, put all developers in it, and assign permission sets to the group instead of individual users. Except... that's not how it works either. You don't assign permission sets to groups. You assign groups to accounts with specific permission sets. Let me show you what I mean: The Correct Mental ModelIt took me about a month to understand this relationship. Every combination has to be explicit. If you want Alice to access three accounts, you need three separate assignments, even if she's in a group. The office analogy is what finally made it click: Traditional IAM thinking: "Alice is a developer, so she gets developer keys that work in the development office." Identity Center reality: "Alice is a developer, so she gets developer keys for the development office, read-only keys for the production office, and admin keys for the research office. Each key only works for one specific office." Here's what this looks like in practice: Same user, three different levels of access, based on which account she's accessing. The mental shift took time because it's fundamentally different from how IAM works. With IAM, you attach policies to users and they work within that account. With Identity Center, you're defining relationships between users, accounts, and permission sets. Once I understood this, the office analogy made perfect sense:
Now when I set up new environments, I think in terms of:
The confusion happens because you have to be explicit about every relationship. There's no "default access" or "inherit from parent" like you might expect. Everything is intentional and specific. Why This Matters in Practice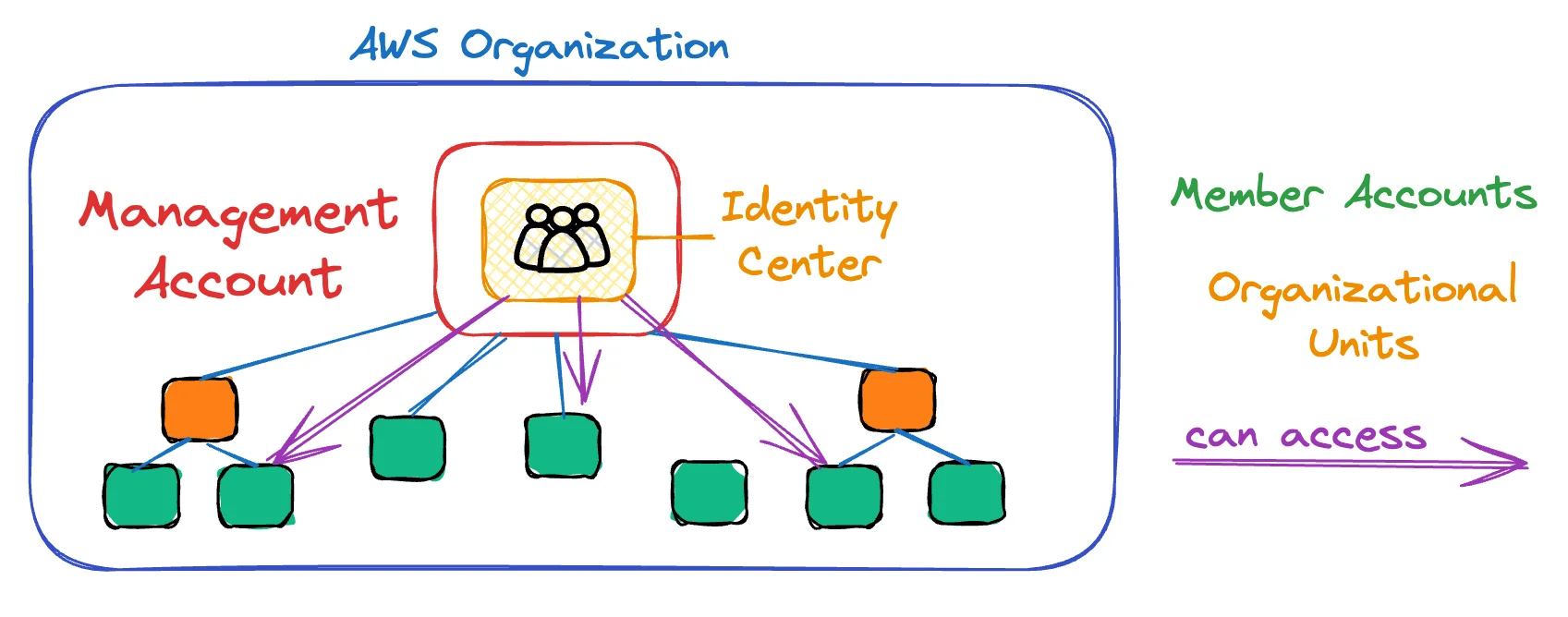
The Real User JourneyHere's what happens when a developer needs to deploy to staging:
This all happens transparently. The developer doesn't need to understand SCPs or know which account they're in. They just can't do the dangerous stuff. Consolidated EverythingOne massive benefit people miss: consolidated billing and monitoring. Consolidated Billing - The Financial SuperpowerConsolidated brings all your costs together. 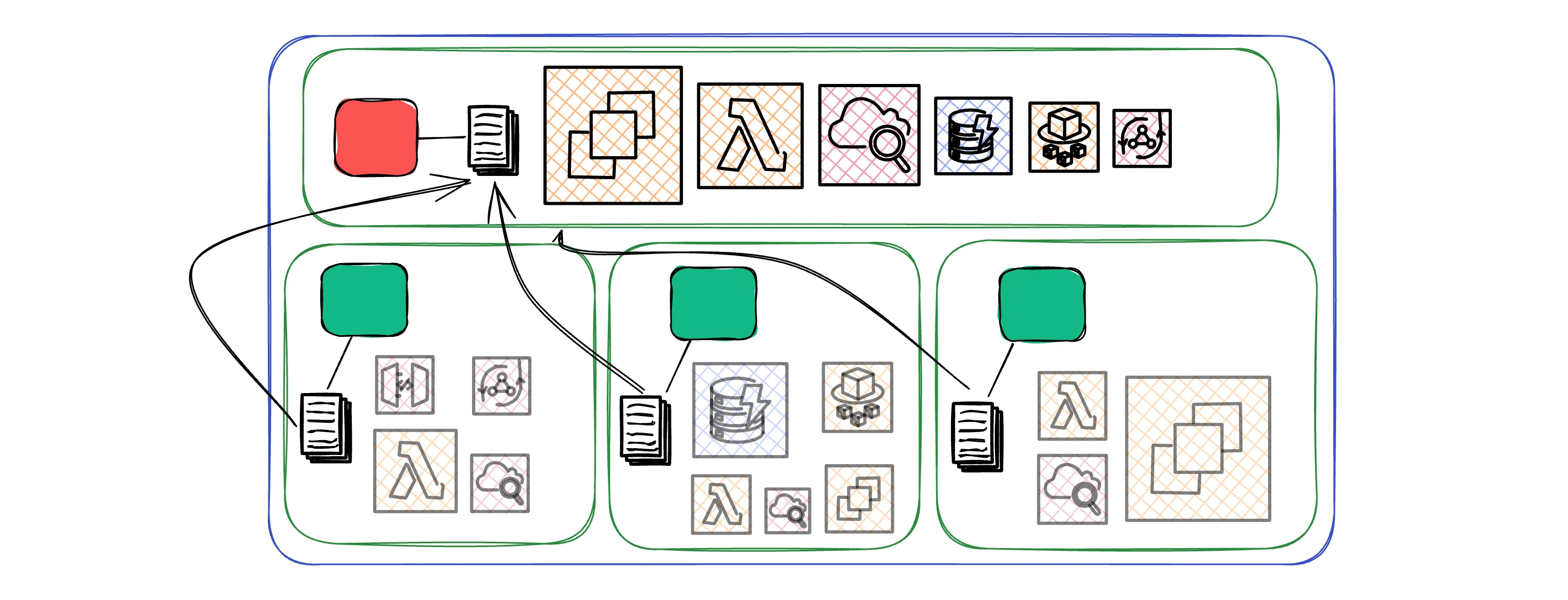
Practical Example: Before Organizations: You had 3 separate AWS accounts with bills of $200, $150, and $300. After Organizations: One $650 bill with better visibility into where every dollar goes, plus automatic volume discounts. Consolidated MonitoringWith consolidated monitoring, you can see everything in one place.
The Organizational Structure That WorksWhether you're a solo developer or managing a small team, here's a structure that scales: Minimal setup (perfect for solo developers or small teams): Recommended setup (adds staging for safer deployments): For teams of 5+ people: Sandbox Account gets loose SCPs so people can experiment. Production gets strict SCPs so no one can accidentally break things. Staging (if you use it) gets production-like SCPs to catch issues early. The Three Permission Sets You Actually NeedForget about creating 15 different permission sets. Start with these three and you'll cover 90% of your use cases: 🔍 ReadOnly 🔨 Developer ⚡ Admin The Stuff You Still Have to Do ManuallyI wish I could tell you this setup runs itself, but that would be lying. Here's what you'll still be doing the old-fashioned way: 👥 Adding New People 🏢 Creating New Accounts ⚙️ Permission Updates 🔒 SCP Changes What You Can Automate (Eventually)Once your foundation is solid, this is where the fun begins: 🏭 Account Factories 🚨 Compliance Monitoring 💰 Smart Budget Alerts The Monitoring You Actually NeedSet up alerts for organization-level events:
Here's a simple EventBridge rule that sends Slack notifications for any organization changes:
JSON
Connect this to SNS, Lambda, and Slack. Now you know immediately when someone changes your organization structure. What This Actually Prevents
The Real Benefits After 6 MonthsAfter running this setup for a while, you'll notice:
The setup takes a few days. The benefits last for years. Common Mistakes and How to Avoid ThemThere's a lot of stuff you can automate, but there's also a lot of stuff you can't. And a lot of stuff you can make mistakes with. Let's go through some of the most common mistakes and how to avoid them. The SCP LockoutThis is the classic mistake. You create an SCP that's too restrictive and apply it to the root of your organization. Suddenly no one can do anything, including you. What happens: You create an SCP that denies all actions. You attach it to the root. Now nobody can do anything, even in development. How to avoid it:
The Permission Set ExplosionYou start with simple permission sets: Developer, Admin, ReadOnly. Then someone needs "Developer but with S3 admin access." So you create "DeveloperWithS3." Then "DeveloperWithS3AndRDS." Soon you have 20 permission sets and no idea which is which. How to avoid it:
Starting Too ComplexYou read about AWS Control Tower, AWS Config, GuardDuty, and Security Hub. You try to implement everything at once. Nothing works and you give up. How to avoid it:
When Things Go Wrong (And They Will)Here are the most common issues I've seen and how to fix them: "I can't access my account after setting up SCPs"🚨 Symptom: You applied an SCP and now you're locked out. 🔧 Fix: Log into the management account and detach the problematic SCP. Test it on a throwaway account next time. "Identity Center login works but I can't access anything"🚨 Symptom: You can log into the portal but clicking account tiles gives errors. 🔧 Fix: Check that you've assigned the user to accounts with permission sets. An empty assignment means no access. "Complains about frequent re-authentication"🚨 Symptom: People have to log in every few hours. 🔧 Fix: Increase session duration in your permission sets. The default 1 hour is definitely too short for most workflows. Pain point: it's not possible to have anything longer than 12 hours. "My SCPs aren't working"🚨 Symptom: You applied an SCP but people can still do the blocked actions. 🔧 Fix:
What I Wish I'd Known Before StartingI've now set up AWS Landing Zones three times - twice for clients, once for my own projects. Here's what I wish someone had told me before I started: It's going to take longer than you think. Even with Terraform, budget a full week, not a day. Between waiting for account creation, debugging SCP conditions, and fighting with Identity Center assignments, things pile up. Start smaller than you want. I tried to build the perfect setup the first time. Three OUs, five permission sets, complex SCPs. I spent more time managing the setup than actually building software. Start with one sandbox account and one production account. Add complexity when you actually need it. Nobody cares about your beautiful organization structure. Developers want to deploy code and see logs. They don't care about your perfectly nested OUs or elegant permission set naming conventions. Build for them, not for the AWS architecture diagrams. The real value shows up in weird places. You think you're building this for security and compliance. But the biggest win ends up being consolidated billing. Or not having to rotate access keys every quarter. Or being able to answer "who can access production?" in five seconds instead of five hours. Some fights aren't worth having. Yes, you can lock down IAM so developers can't create roles. But then you spend all day creating roles for them. Sometimes it's better to give them PowerUserAccess and sleep well knowing SCPs will catch the dangerous stuff. When Landing Zones Aren't Worth ItBe honest with yourself about whether you actually need this. Skip it if:
Do it if:
The setup overhead is real. Don't create complexity you don't need. The Stuff That Still SucksEven with a perfect Landing Zone setup, some things still suck:
My Current SetupAfter three attempts, here's what I actually run: 👥 Accounts:
🔑 Permission Sets:
🔒 SCPs:
That's it. Four accounts, three permission sets, three SCPs. It handles a team of a few developers working on a dozen different projects. Start HereIf you're convinced you need this, start with the absolute minimum:
Don't create multiple OUs. Don't build complex permission sets. Don't try to automate everything with Terraform yet. Get the basics working first. Then add one thing at a time, only when you actually need it. The Real QuestionThe question isn't "should I build an AWS Landing Zone?" It's "what problems am I actually trying to solve?" If you're trying to solve credential management, start with Identity Center. If you're trying to prevent expensive mistakes, start with simple SCPs. If you're trying to organize projects, start with separate accounts. Don't build the whole thing because some blog post (including this one) told you to. Build the parts that solve real problems you're actually having. The best Landing Zone is the one that gets out of your way and lets you build software. Everything else is just complexity for the sake of complexity. Now go build something. 🚀 SummaryThat's it for this newsletter! We’re talking about how starting AWS the wrong way can turn into a total account management nightmare and why building a proper landing zone from the start saves you tons of pain later. Have you ever felt buried under IAM policies across multiple accounts? See you soon 👋🏽 Sandro & Tobias |
AWS for the Real World
We teach AWS for the real world - not for certifications. Join more than 10,500 developers learning how to build real-world applications on AWS.
AWS FOR THE REAL WORLD ⏱️ Reading time: 12 minutes 🎯 Main Learning: Run an always-on AI agent on a $5 Lightsail instance with zero open ports, SSM access, and GitHub as a time machine for your agent's brain 📝 Blog Post 🎬 Watch on YouTube Hey Reader 👋🏽 the past weeks there is obviously one driving topic: OpenClaw 🦞 We love seeing that a developer from our neighbor country 🇦🇹 built a tool that got so MUCH hype. That is why we needed to try it out as well! While I (Sandro) added OpenClaw to my...
AWS FOR THE REAL WORLD ⏱️ Reading time: 8 minutes 🎯 Main Learning: How to securely connect Claude Code to a private RDS database using MCP, SSM tunnels, and VPC endpoints 📝 Blog Post 💻 GitHub Repository 🎬 Watch on YouTube Hey Reader 👋🏽 AI coding assistants are great. If you give them the right context. Your database schema is one of the most valuable pieces of context you can provide. But there's a problem: your RDS is in a private subnet. As it should be. So how do you connect Claude Code to...
AWS FOR THE REAL WORLD ⏱️ Reading time: 8 minutes 🎯 Main Learning: How to pause Step Function workflows for human approval using the callback pattern 📝 Blog Post 💻 GitHub Repository 🎬 Watch on YouTube Hey Reader 👋🏽 I've used this pattern in almost every project I've built. Whenever you need a human in the loop - approvals, reviews, manual checks - and you still want to see what's happening, Step Functions are perfect. Lambda is my go-to for almost everything. APIs S3 triggers event consumers...