Simplify Cross-Account Logging in 5 Steps Now! 📜
|
AWS FOR THE REAL WORLD
⏱️
Reading time: 4 minutes
🎯
Main Learning: AWS CloudWatch log centralization makes cross-account logging simple. Learn how to set it up, avoid gotchas, and query logs across your organization.
Hey Reader 👋🏽 another week, another newsletter about CloudWatch. This time we're talking about a rather new feature: Log Centralization. But quick question before we dive into this week’s CloudWatch deep dive… We’re 6 weeks out from 2025 (wild, right?) and I’m curious: If You Could Achieve Just One Thing with AWS Next Year, What Would It Be?
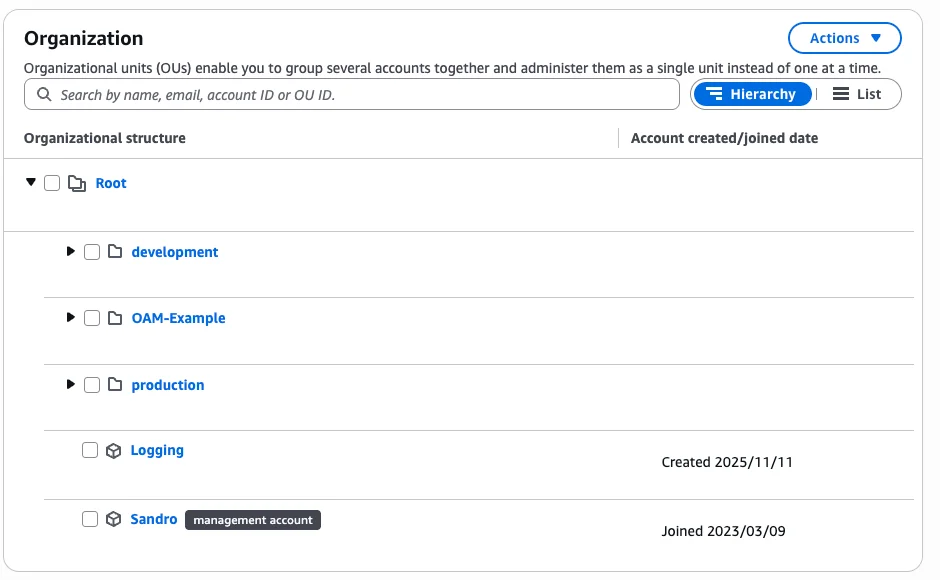
(Takes 2 seconds, helps us create better content for you in 2026 😊) Alright, onto this week's CloudWatch feature... We all know, that we should have a dedicated logging account. All logs should flow into this account. There are several reasons for having that:
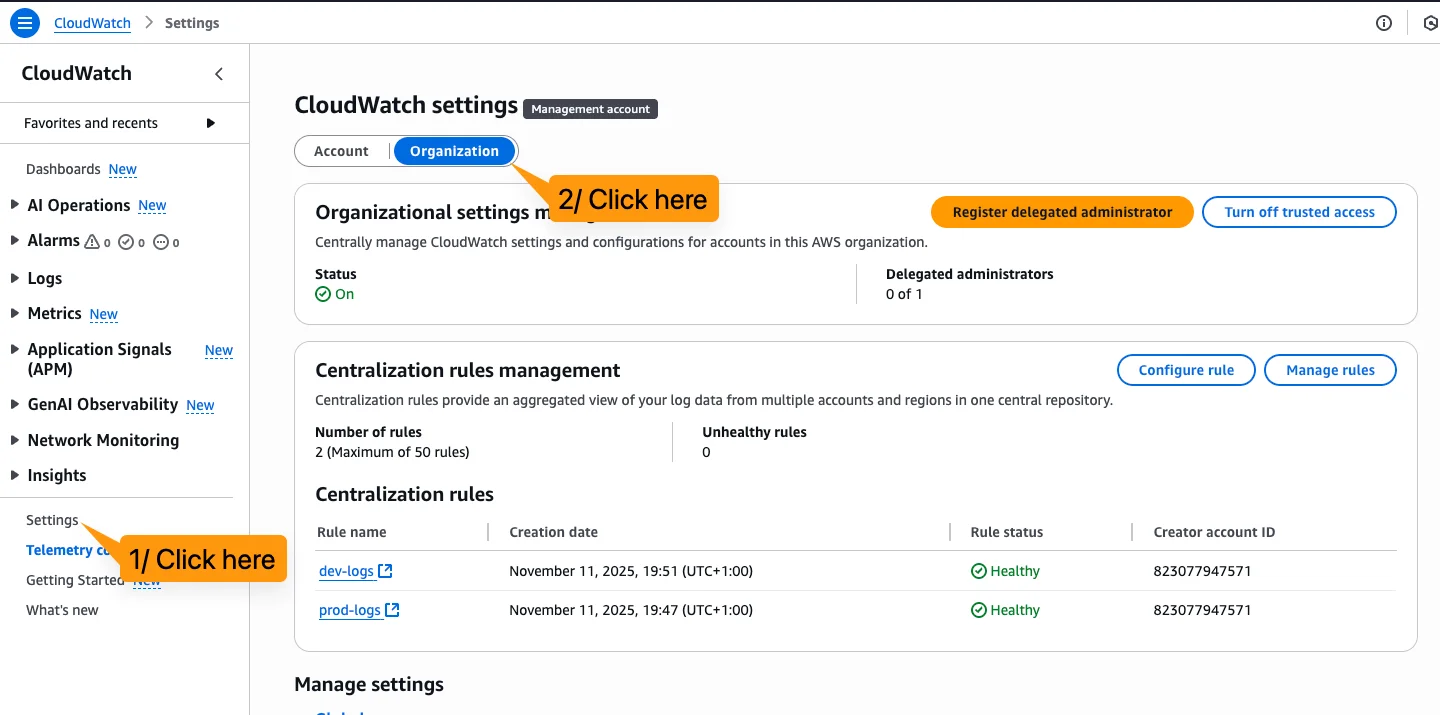
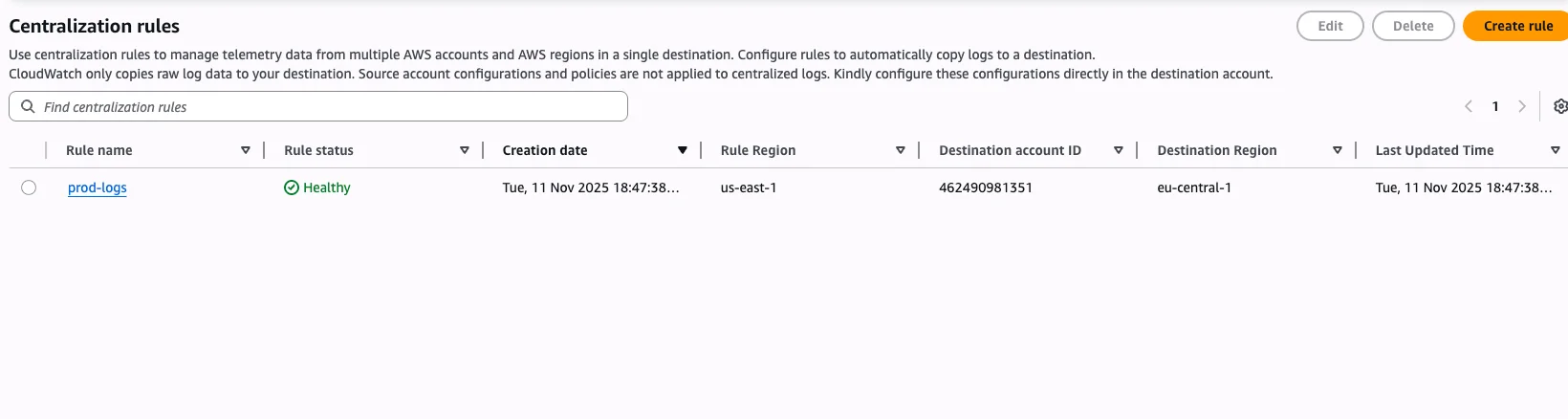
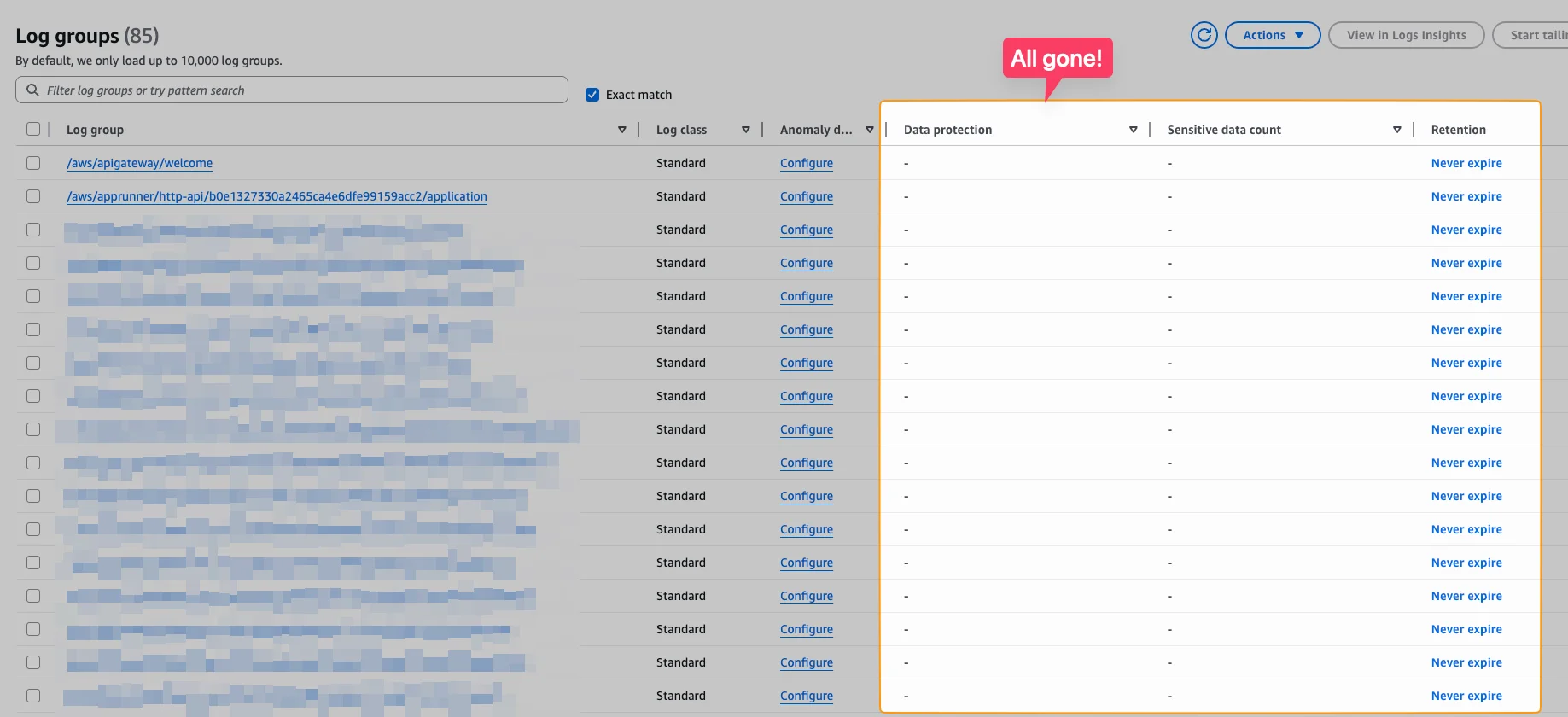
But the ways of doing that where quite complicated in the past. It typically was either a self-built solution with subscription filters and Kinesis. Or you've used the Observability Access Manager. That is where Log Centralization comes in. This features was just launched a couple of months ago. If you use an AWS Organization you can use that to centralize all your logs with a simple click! More of that in this week's deep dive!
That's it for this week! Keep an eye out for all the re:Invent launches in the upcoming weeks 👀 Best, Sandro & Tobi |
AWS for the Real World
We teach AWS for the real world - not for certifications. Join more than 10,500 developers learning how to build real-world applications on AWS.
AWS FOR THE REAL WORLD ⏱️ Reading time: 8 minutes 🎯 Main Learning: How to securely connect Claude Code to a private RDS database using MCP, SSM tunnels, and VPC endpoints 📝 Blog Post 💻 GitHub Repository 🎬 Watch on YouTube Hey Reader 👋🏽 AI coding assistants are great. If you give them the right context. Your database schema is one of the most valuable pieces of context you can provide. But there's a problem: your RDS is in a private subnet. As it should be. So how do you connect Claude Code to...
AWS FOR THE REAL WORLD ⏱️ Reading time: 8 minutes 🎯 Main Learning: How to pause Step Function workflows for human approval using the callback pattern 📝 Blog Post 💻 GitHub Repository 🎬 Watch on YouTube Hey Reader 👋🏽 I've used this pattern in almost every project I've built. Whenever you need a human in the loop - approvals, reviews, manual checks - and you still want to see what's happening, Step Functions are perfect. Lambda is my go-to for almost everything. APIs S3 triggers event consumers...
AWS FOR THE REAL WORLD ⏱️ Reading time: 5 minutes 🎯 Main Learning: How to make Claude write production-ready Terraform instead of technical debt 🎬 Watch on YouTube 📝 Blog Post 💻 GitHub Repository Hey Reader 👋🏽 We've been heads-down the past weeks. Preparing the live AMA workshops from Black Friday (sorry for the delay!) and recording new YouTube videos. It's been a lot of fun. Speaking of videos - this week Tobi recorded one you'll want to watch. Here's the problem: LLMs want to close the...