💜 Terraform - The World's Most Used Iac Tool
👀 This is not properly displayed? Read all of our issues online! 💡
Hi Reader 👋🏽
In this issue, we will explore the basics of Terraform, an open-source Infrastructure-as-Code (IaC) tool, and how it can simplify and automate the provisioning and management of your cloud infrastructure.
Join us as we uncover the key concepts and best practices to help you get started with Terraform and unlock its full potential.
🚨 P.S.: If you make it through this issue, we'll farewell you with some fascinating facts about Terraform that could definitely blow your mind even more and two sweet discounts 🍬 you'll hopefully enjoy! 💛
Next Project: The CloudWatch Book 📕
First of all, some news from us. We decided to tackle the next project which will be 🥁 the CloudWatch Book. If you're interested in the project check out the link.
Without further ado, let's get going! 🌟
Infographic
Before jumping in, have a look at the most important things about Terraform in our infographic below.
A Little Reminder: What's IaC and why do we need it?
Before the cloud, changing the hardware your application runs on was difficult. But now, you can easily scale your application up or out, without any upfront costs.
You can provision infrastructure globally and delete it quickly when you no longer need it.
This has created a need for tools that can manage infrastructure resources programmatically.
With Infrastructure-as-Code tools, you can define all your infrastructure resources as code, alongside your application code.
 |
Terraform stands out as one of the leading and highly adaptable IaC tools available today.
P.S.: If you want to delve deeper into the foundational aspects of IaC on AWS, we recommend checking out our previous blog posts about the history of IaC.
Declarative vs. Imperative Approaches
There are two types of IaC tools: declarative and imperative.
- Declarative tools define the desired state of the infrastructure without specifying the steps. Examples include Terraform and CloudFormation, which use YAML or JSON.
- Imperative tools list the commands needed to achieve the desired state. They often use Object-Oriented languages like TypeScript.
Declarative tools focus on defining the desired state of the infrastructure, while imperative tools explicitly list the commands needed to achieve that state. Each approach has its own benefits and considerations to take into account when choosing an IaC tool.
Key Concepts of Terraform
Terraform stands out as one of the most flexible options available. To fully grasp its capabilities and utilize it effectively, it's important to familiarize ourselves with its key concepts.
Multi-Platform Support via Providers
Terraform offers support for a wide range of cloud providers and services through its provider plugins. In addition to AWS, it also supports GCP, Azure, and other services like NewRelic.
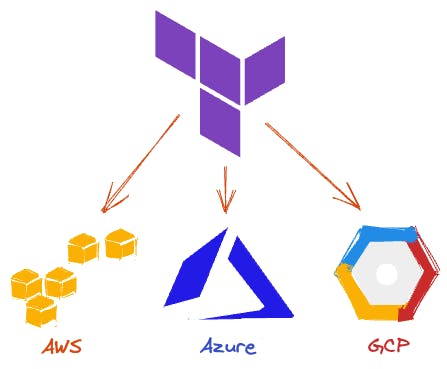 |
This flexibility allows you to build a multi-cloud or multi-platform environment without the need for multiple tools.
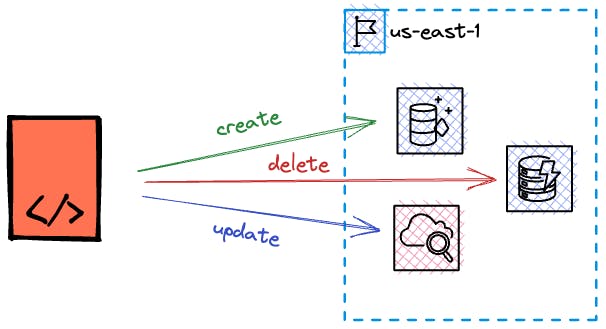
Remote Tracking of Infrastructure State
One of the key features of Terraform is its ability to keep track of the state of your infrastructure. Whenever you make changes to your infrastructure by creating, updating, or deleting resources, Terraform saves the current state.
This means that Terraform remembers which resources are currently created and their configurations. This enables Terraform to determine the necessary changes required to reach the desired state, ensuring consistency and accuracy.
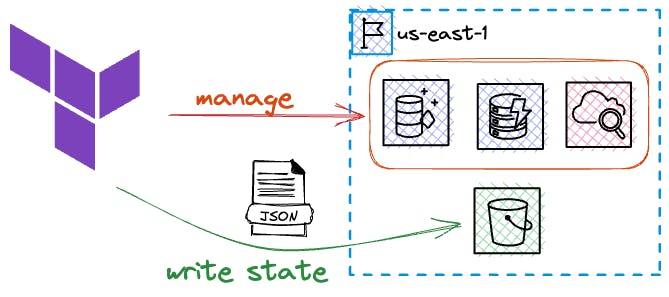 |
The infrastructure state can be stored remotely, such as in an S3 bucket. This allows you to run Terraform from different locations while maintaining the same results.
Abstractions and Blueprints via Modules
Terraform modules provide a way to create blueprints for your infrastructure and encapsulate configurations.
 |
This allows you to create complex infrastructure setups hidden behind an abstraction layer. Modules also enable you to reuse these setups in different environments.
Previewing Changes
Terraform offers two important commands: plan and apply.
The plan command previews the changes that Terraform would execute. It helps prevent unintended changes and allows for safer and more controlled updates. The previewed plan can be saved locally and executed as-is.
The apply command executes all the changes indicated by Terraform to achieve the desired state of the infrastructure.
More Features
Terraform comes with a lot of features. Let's explore some of the most important ones!
Modules
Terraform modules provide a way to encapsulate and reuse infrastructure configurations, simplifying the management of complex environments and promoting the adoption of best practices.
In the example graphic below, we have two separate modules that define blueprints for different components:
- Module 1: Frontend Distribution - Utilizes CloudFront, IAM, and S3 to build a frontend distribution.
- Module 2: ECS-based Service - Uses Fargate, IAM, and an Elastic Load Balancer to create an ECS-based service.
By modularizing these configurations, we can easily reuse them, promote code sharing, and ensure adherence to best practices.
Resource Outputs
Each cloud platform has its own unique way of identifying resources, which is important for coupling components together.
For instance, AWS uses Amazon Resource Names (ARNs) to identify resources. If you want to grant access to a DynamoDB table while following the principle of least privilege (granting only necessary permissions for a user or service to perform its tasks), you need to include the corresponding ARN in the IAM policy.
To address this, Terraform provides outputs. You can reference the outputs of resources that are only available after the resource is created before Terraform executes.
Terraform determines resource dependencies by creating a Dependency Graph. This graph helps Terraform understand which resources rely on others and in what order they need to be created.
Let’s take a look at an example:
- The IAM policy references the ARN of the DynamoDB table.
- The IAM role relies on the IAM policy.
- The Lambda function needs to have the IAM role attached.
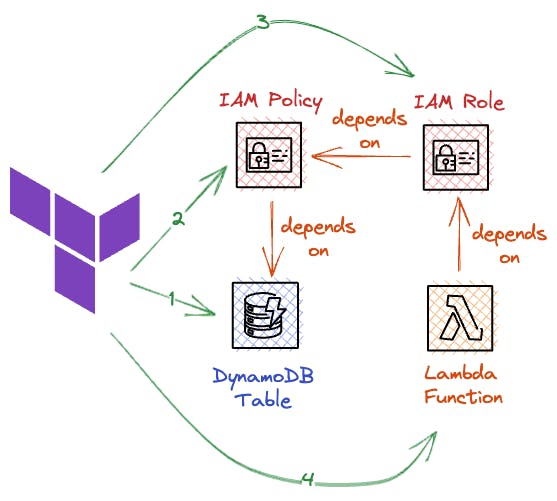 |
In this case, our dependency graph starts with the Lambda function and ends with the DynamoDB table. The table needs to be created first, and the Lambda function should be created last.
Terraform automatically detects and handles these dependencies, ensuring the correct order of resource creation.
HCL and Expression Functions
Terraform files utilize HashiCorp’s configuration language HCL (HashiCorp Configuration Language) for defining their structure. This language incorporates expression functions that provide a range of powerful capabilities for creating resources and values dynamically, manipulating data structures, and performing simple or complex calculations within your Terraform code.
Some examples of included expression functions are:
- regex(string, pattern) : This function returns true if the given string matches the specified regular expression pattern.
- join(separator, list) : This function returns a string that is the concatenation of the elements in the given list, separated by the specified separator.
The Terraform documentation contains a comprehensive list of all available expression functions.
By using expression functions, you can enhance the dynamism and flexibility of your Terraform code, thereby reducing the need for repetitive or manual tasks.
Meta Arguments
In Terraform, a resource block typically corresponds to a single infrastructure resource. However, there are cases where we need to create multiple objects that share similar characteristics without duplicating the code.
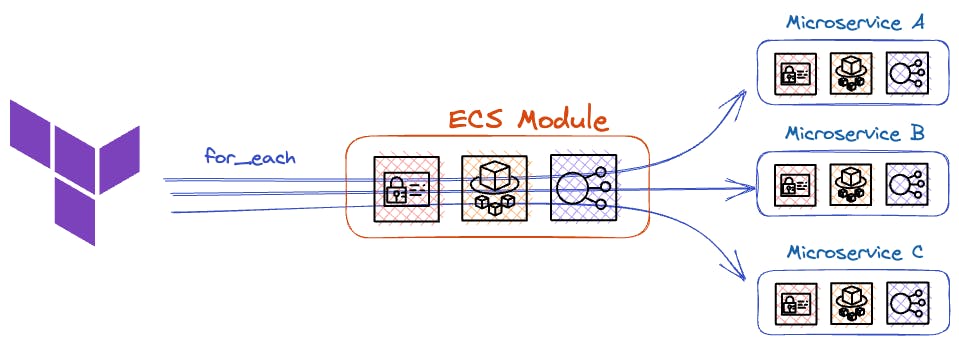 |
To address this properly, we can utilize meta arguments such as for_each .
Dynamic Blocks
The for_each function allows us to dynamically generate multiple resources. This functionality can also be applied to blocks within our resources by combining them with dynamic blocks.
For instance, we can attach multiple EBS volumes to an EC2 instance based on a variable:
In this example, we provide a list of complex objects (a map in Terraform) to configure our EC2 instance. We iterate over each value using the for_each function and assign the corresponding field values to the EBS configuration.
We also utilize the lookup expression, which retrieves the value for a given key (in this case, the IOPS value via "iops") or returns a fallback value of null.
If an empty list is passed, the dynamic block will be empty, resulting in no EBS volumes being added.
Managing Multiple Environments
Terraform provides a convenient way to efficiently handle multiple environments, such as development, staging, and production, by utilizing its module-based approach.
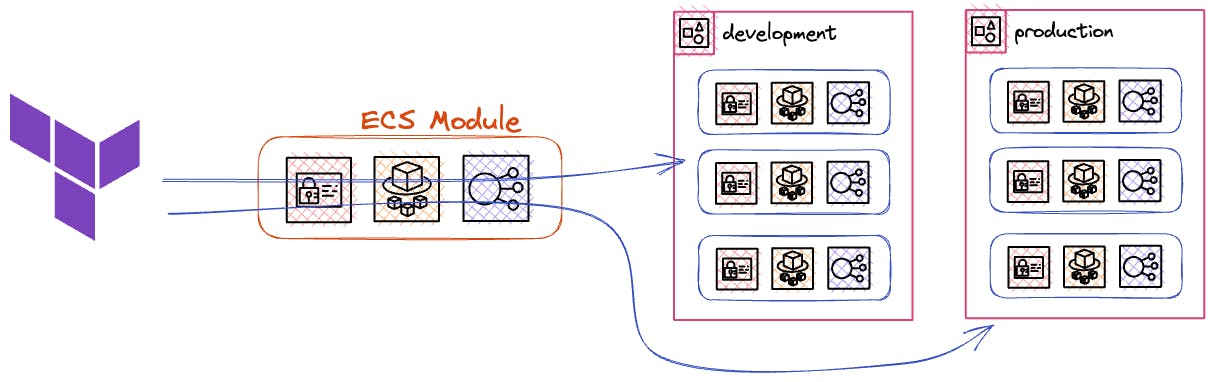 |
To create multiple environments, you have two options: utilizing different workspaces or employing separate state files. This approach not only simplifies the deployment process but also allows for the seamless configuration of various AWS regions. By duplicating the main region, each region can receive an exact replica of the original setup.
Valuable Resources
Useful References for Terraform Terraform is a complex and extensive ecosystem that thrives on community collaboration. Here are some valuable resources to explore:
- 📚 Module Registries: A wide range of module blueprints in both private and public registries. These registries provide a wealth of pre-built infrastructure components that can be easily integrated into your projects.
- 🛠️ Enhanced Tools: Additional tools that complement and enhance the functionality of Terraform. These tools offer advanced features and capabilities to streamline your infrastructure provisioning process. One great example is infracost, which helps to know the costs of cloud resources even before launching them. 💸
- 👥 Community Resources: Tap into the vast knowledge and experience of the Terraform community via resources, including forums, documentation, tutorials, and case studies.
For a comprehensive list of curated resources, visit the awesome-terraform 🔗 repository on Github. This repository serves as a centralized hub for discovering high-quality tools, modules, and community contributions.
Other Great IaC Tools
Besides Terraform, there are many other IaC tools that are worth exploring:
- AWS CloudFormation: An AWS-native IaC tool developed by Amazon. It uses YAML files to define resources and manages them in a CloudFormation Stack. It tracks the state of resources and can perform rollbacks during updates.
- AWS Cloud Development Kit: An abstraction layer on top of AWS CloudFormation. It supports multiple programming languages and offers high-level abstractions for infrastructure components. CDK deploys infrastructure using AWS CloudFormation.
- Pulumi: An open-source IaC platform that supports multiple cloud providers, including AWS, Azure, and Google Cloud Platform. It allows developers to use their preferred programming language and offers features like infrastructure testing and rollbacks.
- Serverless Framework: A declarative IaC framework that focuses on serverless architectures, particularly AWS Lambda. SF provides a high level of abstraction and simplifies the configuration of serverless components like AWS API Gateway. It uses CloudFormation to manage the infrastructure.
More Mindblowing Facts
As promised, there's even more to know.
- 🌟 Terraform is platform-agnostic: While many people know that Terraform can manage a variety of service providers, it's less known that it's completely platform-agnostic. This means you can use it to manage a diverse set of infrastructures like public clouds, and private clouds, or directly with software APIs on your local machine.
- 🔌 Terraform uses a plugin-based architecture: This means that it's not just limited to the providers that HashiCorp (the company behind Terraform) supports. If you have a service that Terraform doesn't support, you can write your own provider plugin.
- 🛠️ Terraform isn't just for infrastructure: While Terraform is often used for spinning up servers or containers, it can also manage higher-level components such as DNS entries, email provider settings, or page rules on Cloudflare. This makes it a versatile tool for a wide range of use cases.
After working with Terraform for five consecutive years, we love it even more than in the beginning!
If you haven't started to use an Infrastructure-as-Code tool yet: today is the day and Terraform will be an awesome choice! 🚀
Beyond AWS Fundamentals
This week, we're introducing Yan Cui, a well-known AWS Serverless Hero and the brilliant mind behind the Production-Ready Serverless* class as well as the books Testing Serverless Architectures* & The AppSync Masterclass*.
Yan also has a podcast realworldserverless where our one and only Sandro Volpicella just recently talked about AWS Fundamentals and our upcoming project, the CloudWatch Book. Watch for an upcoming episode.
With his expertise, clients have achieved remarkable results by accelerating their projects and achieving more with less effort. If you are eager to enhance your AWS skills and gain insights into building exceptional serverless applications, make sure to join his newsletter! 💛
You'll receive valuable tips, step-by-step tutorials, and practical advice, all conveniently delivered straight to your inbox every week.
🎉 Bonus #1: if you use the code HALLOWEEN23 in the checkout, you'll get a 30% discount - applicable for every product by Yan! 🎃 If you're reading this newsletter issue well after Halloween, you can also use AWSFUNDAMENTALS to get a 15% discount!
🎁 Bonus #2: with the code NEWSLETTER15 you'll get a 15% discount for all of our AWS Fundamentals products 🙏
* if you purchase one of Yan's books or courses through our links, we'll receive a small portion of the revenue which helps to keep this newsletter and other content free 💛
That's all for today!
We wish you all the best and a great start to the week!
Tobi & Sandro 👋
P.S.: If you've liked this issue and you're interested in learning more about Terraform, be sure to check out our starter guide which also includes hands-on examples! 🧑💻 👩💻
Still hungry for AWS content? Have a look at our blog! 📚 ↓
AWS for the Real World
We teach AWS for the real world - not for certifications. Join more than 10,500 developers learning how to build real-world applications on AWS.
AWS FOR THE REAL WORLD ⏱️ Reading time: 8 minutes 🎯 Main Learning: How to securely connect Claude Code to a private RDS database using MCP, SSM tunnels, and VPC endpoints 📝 Blog Post 💻 GitHub Repository 🎬 Watch on YouTube Hey Reader 👋🏽 AI coding assistants are great. If you give them the right context. Your database schema is one of the most valuable pieces of context you can provide. But there's a problem: your RDS is in a private subnet. As it should be. So how do you connect Claude Code to...
AWS FOR THE REAL WORLD ⏱️ Reading time: 8 minutes 🎯 Main Learning: How to pause Step Function workflows for human approval using the callback pattern 📝 Blog Post 💻 GitHub Repository 🎬 Watch on YouTube Hey Reader 👋🏽 I've used this pattern in almost every project I've built. Whenever you need a human in the loop - approvals, reviews, manual checks - and you still want to see what's happening, Step Functions are perfect. Lambda is my go-to for almost everything. APIs S3 triggers event consumers...
AWS FOR THE REAL WORLD ⏱️ Reading time: 5 minutes 🎯 Main Learning: How to make Claude write production-ready Terraform instead of technical debt 🎬 Watch on YouTube 📝 Blog Post 💻 GitHub Repository Hey Reader 👋🏽 We've been heads-down the past weeks. Preparing the live AMA workshops from Black Friday (sorry for the delay!) and recording new YouTube videos. It's been a lot of fun. Speaking of videos - this week Tobi recorded one you'll want to watch. Here's the problem: LLMs want to close the...